Bennington State Bank ACH Newsletter
July 27, 2023
Thank you for choosing The Bennington State Bank for your commercial banking needs! The latest ACH Newsletter is filled with helpful information and exciting changes. The BSB Treasury Team is here to help align our services with your business needs!

The main differences between ACH vs check payments are cost, security, and speed of delivery. ACH transfers are electronic whereas checks are physical documents that are manually sent – making ACH transfers a safer and more efficient payment method. Because it eliminates the cost and time associated with paper checks, ACH services can help improve your business cash flow, whether you’re issuing or receiving many checks, making payments, or processing payroll.
Best Practices
Here are three best practices to help clean up your data this spring:
- Check user settings and clean out any outdated privileges
- Update weak or old passwords and make sure to turn on Two-Factor Authentication
- Check your devices and software to make sure they are up to date
SEC Codes
Standard Entry Class (SEC) Codes – Each ACH transaction must be accompanied by a three‐character identifier referred to as a standard entry class (SEC) code. An SEC code defines how authorization for the transaction was obtained. Some SEC codes may only be used for transactions sent to a consumer account; others may only be used for transactions sent to a business/corporate account. Some codes may be used for transactions sent to both types of accounts. NOTE: SEC codes must be used appropriately and in accordance with the NACHA Rules.
The chart below outlines and defines the most common SEC codes being used today in the ACH network.
Bennington State Bank has the right to ask for proof of verification of methods used to gather ACH information.
| ACH Application SEC Code | Application Use |
|---|---|
| PPD | Payment from or deposit to a consumer (person) |
| CCD | Payment from or deposit to a corporation (business |
| CTX | Corporate Trade Exchange |
| WEB | Internet Initiated entries |
| ARC | Accounts receivable entries (check conversion to ACH) |
| BOC | Back Office Entries (check conversion to ACH) |
| POP | Point-of-Purchase (check conversion to ACH) |
| RCK | Re-Presented check collection |
| TEL | Telephone Initiated entries |
Web entries
For those who create ACH files using data collected via the internet/mobile/web/email (not using a standard form), you must originate entries using the WEB SEC code. This is accomplished by selecting the proper SEC Code when creating an ACH batch. Prenotes and all transactions going forward for those collected in this matter, need to use the WEB SEC code.
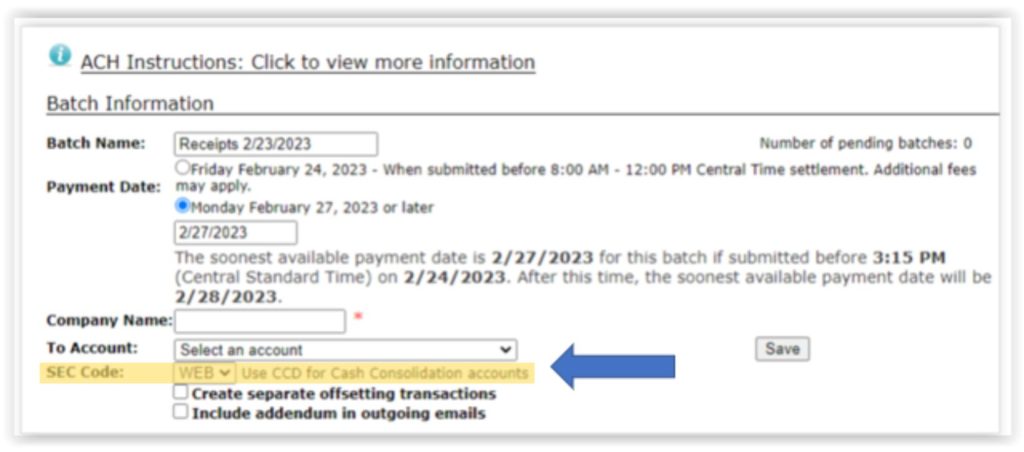
Additional requirements for WEB:
- Use a commercially reasonable fraudulent detection system that validates the account to be debited for the first use of such account number. Methods include using pre-notes, micro-transactions, or using a validation service provided by an ODFI
- Verify the receiver’s identity
- Verify the routing number associated with the entry is valid
- Conduct an annual audit of data security practices for the receiver’s financial information
Return Rates
NACHA Rules require that banks monitor their ACH Origination customer’s return rate level.
The Unauthorized Entry Return Rate must be .5% or less. This includes returns made to you for the following reasons:
- R05 – Unauthorized Debit to Consumer Account using Corporate SEC
- R07 – Authorization Revoked
- R10 – Customer Advises Not Authorized, Improper, or Ineligible
- R29 – Corporate Customer Advises Not Authorized
- R51 – Item is Ineligible, or RCK Entry is Improper
Administrative Return Rate of 3.0% or less. This includes returns made to you for the following reasons:
- R02 – Account Closed
- R03 – No Account/Unable to Locate
- R04 – Invalid Account Number
The overall Return Rate must remain at 15.0% or less.
Exceeding these limits can cause NACHA to assess fines. In such an event, the bank will discuss action plans with the ACH Originator including but not limited to terminating the contract.
Prenotes vs. Micro Entries
A prenotification is a zero-dollar entry generated to validate an account held at a Receiving Depository Financial Institution (RDFI). Companies may originate prenotifications; however, they are not required under the Rules. A prenotification is a tool to ensure the account information given by the receiver is accurate prior to initiating a live dollar transaction. If the Originator chooses to initiate a prenotification, they must wait three (3) banking days prior to initiating the live dollar transaction.
Micro-entries Rules Phase 2
Beginning with the Rules change, Phase 2 of the Micro-Entries Rule (soon to be Subsection 2.7.5 of the ACH Rules) took effect on March 17, 2023. Phase 1 of the Rule, which took effect on September 16th, 2022, defined Micro-Entries officially as “ACH Credits less than $1 and any offsetting ACH Debits, used for the purpose of verifying a Receiver’s account” sent by ACH Originators. These are used to send unique offsetting entries that a Receiver can easily see on their account and report back to the Originator for validation. Phase 2, however, implements a new rule that states “an Originator of Micro-Entries must conduct commercially reasonable fraud detection on its use of Micro-Entries, including by monitoring the forward and return volumes of Micro-Entries”. Furthermore, the detection and reporting are intended to minimize the incidence of fraud schemes that make use of Micro-Entries, establish a baseline of activity, and should be monitoring volumes instead of entry-to-entry reviews.
For more information: 2023 ACH Rules Update for Corporate Originators and Third-Party Senders
NOC- Notification of Change
- BSB will set up users to receive these notifications based on the information you provide while executing your ACH contract. If any changes need to be made to these users, you will need to notify us. It is important that the NOCs are monitored daily and corrections are made timely.
- When ACH information is incorrect, a Notification of Change (NOC) is sent by the Receiving Bank requesting that future entries contain correct information. ACH Rules require you to make the change within six (6) banking days of receiving the information or before another entry is sent.
- The Receiving Bank warrants that the information they provide to you is correct.
Contracts
- ACH Renewals are completed every three years by BSB’s Treasury Department.
- ACH Contracts should be signed by an individual who has been given the authority to enter the business into contracts per the operating agreement/by-laws.
ACH Verification
- If you have chosen to send ACH verifications after a batch is submitted, please send those verifications to:
- services@bsbks.com
- Fax to 785-827-7577
If you would like to purchase the 2023 Nacha Operating Rules and Guidelines: click here.

How does Bennington State Bank help combat fraud?
Fraud is something we all share responsibility in combatting. Fraudsters will always seek new ways to exploit people’s private information. Cybercrime and fraud prevention is an ever-changing and evolving field based on varied tactics used by fraudsters. While fraudsters will always seek to conduct new fraud forms, you can be better prepared to mitigate their risks. One place to start is being aware of the most frequent fraud attacks today. Here are the top 10 biggest fraud trends you need to know for 2023.
BSB’s Online Banking system utilizes multi-factor authentication through a secure access code that provides a one-time passcode via an application on your cellular device, computer, or tablet. If Two-Factor Authentication does not suit your needs, BSB offers tangible tokens for a $35 fee to create the passcode whenever you log in.
BSB also establishes batch limits as an additional security measure. This limit is set by the bank based on your company’s needs.
BSB suggests monitoring your accounts online daily. The sooner ACH fraud is detected, the more successful the bank will be in assisting to recover any potentially lost funds.
BSB encourages companies to have a separation of duties for ACH processing, in which one employee generates the ACH batch and the system requires a secondary employee to log in and approve the ACH batch. Dual-control procedures such as this go a long way in preventing ACH origination fraud.
Top 10 Fraud and Identity Trends 2023
1. Automation
Automation makes it easier for criminals to exploit users’ accounts while remaining undetected, increasing the risk of fraud. With automation, fraudsters use software or bots to accomplish tasks that otherwise require human intervention, thus covering more ground.
For example, credential stuffing is the act of testing stolen or leaked credentials on websites and services at scale to see if they work on any accounts.
2. Account Takeover
Account takeover (ATO) is a type of identity theft (ID Fraud) that occurs when a fraudster gains access to an individual’s or company’s computer accounts, email accounts, and other personal information. In a typical ATO attack, hackers use phishing and malware methods to acquire legitimate user credentials or buy them from the dark web; they then use stolen credentials for account takeover.
Automated takeover attacks are carried out using stolen credentials, and organizations are particularly vulnerable to these attacks. A takeover can lead to a variety of crimes and direct financial losses, including:
- Bank account takeovers (Current accounts, Credit Cards)
- Money laundering
- Stealing loyalty or rewards points
- Reselling subscription information
3. Adoption of New Digital Payments and Methods
Digital payment platforms and cryptocurrencies disrupt traditional payments, allowing consumers and businesses to make payments more quickly and efficiently.
Technologies that enable new ways to pay are also open to new avenues of attack from fraudsters, as they use stolen credentials to carry out fraud and ID theft.
Cryptocurrencies, while not quite mainstream in their use yet, are growing in popularity, and the anonymity provided by these currencies makes it easy for criminals to carry out illicit activities.
4. Ongoing Challenge of Balancing Fraud & Customer Friction
Online businesses must balance risk and opportunity when mitigating fraud. In the case of online shopping, the amount of “friction” customers experience during the checkout process correlates with their conversion success.
The balance between friction and fraud becomes even more challenging across multiple channels, such as web, mobile, and point of sale. Merchants and issuers seek alternative authentication solutions (such as passive behavioral biometrics and passwordless authentication via biometrics with liveness detection) to attain this balance to improve customer experience and reduce risk.
5. Rise of Synthetic Identities
According to the McKinsey Institute, synthetic identity fraud is the fastest-growing type of financial crime in the United States and is also on the rise around the globe. Indeed, synthetic identity fraud comprises 85% of all fraud right now.
With this type of fraud, fraudsters create new identities by piecing together elements of a person’s personal information and combining them with false identifiers. Essentially, they take bits of legitimate data, add fictitious information, and create a new identity. Organizations are struggling to prevent synthetic identity fraud; after all, the whole point of synthetic identity fraud is to create a synthetic victim that does not exist in real life.
6. Escalating Cost of Fraud
The total cost of fraud is becoming a genuine concern, from fraud losses, prevention tools, and headcount costs to the customer lifetime value impact. It’s estimated that Fraud loss is $5.4 trillion globally; according to the University of Portsmouth, fraud accounts for approximately $185 billion in losses in the U.K. and a 9.9% increase in the cost of fraud for U.S. financial services firms.
Why the increase? As more and more people have turned to online and mobile channels to shop, fraudsters again have followed, thus the increase in fraud losses and associated costs with fighting fraud.
7. Growing Need for Multi-Layered Fraud Assessment
The digitization of e-commerce and banking is a well-established trend that shows no sign of abating; in parallel, fraud across these digital channels has remained a constant and relentless issue.
On the other hand, fraud prevention leaders are generally trying to defeat fraudsters with limited and siloed fraud management capabilities.
To achieve the best fraud prevention results, fraud prevention leaders must orchestrate all relevant data points, risk signals, and customer data to form a centralized and balanced response that reduces risk, customer friction, and associated prevention costs.
8. Targeted Attacks
Another growing threat is targeted attacks, which occur when cybercriminals compromise a target entity’s entire infrastructure, including its network and computer systems. They can conduct such attacks anonymously and over a long period, gaining access to critical financial data and causing significant losses for institutions and constituents.
Targeted attacks occur in phases, thus less likely of being discovered.
Although targeted attacks typically happen at the entity level and don’t target specific consumers, these attacks put customer information at risk and can harm an organization’s reputation.
9. Heightened Need for Real-Time Risk Assessment
As online and mobile app usage increases, there’s a growing need for comprehensive fraud detection, identity verification, and authentication solutions to unite. Such solutions call for real-time risk assessment that leverages the latest AI, Machine learning, and fraud orchestration tools to manage the customer’s risk collectively and trust, utilizing all associated risk signals to drive fair and balanced customer satisfaction.
10. Account Security
To protect against fraudsters, organizations need to take a layered approach to account security. The culprit behind system attacks is often single-factor authentication methods that result in unauthorized access to accounts, enabling customer account fraud, identity theft, ransomware attacks, and other fraudulent activity, notes the Federal Financial Institutions Examination Council.
With multi-factor authentication, institutions use more than one distinct authentication factor to successfully authenticate customers, such as behavioral biometrics, device id, and biometric authentication.




